OnionShare is an open-source application which enables the average user to anonymously host and transfer files, host their own websites and even chat over the the Tor network. In this article, I’ll provide an overview of OnionShare and it’s purpose, but leave the use-case to the imagination of the reader. We’ll also briefly walk-through some of the key components of the methodology behind Tor’s privacy and go through the installation and setup of the OnionShare client, and I’ll demonstrate each of it’s core capabilities.
Overview
The average user will spend the vast majority (if not all) of their internet usage time on the Surface Web (aka “Clear Web”). As seen in the image below, this includes sites and services which are indexed or marketed by Google, Bing, Yahoo, Yandex, DuckDuckGo and others, which means that they can be found with a simple search. It’s hard to believe given the volume of information available through a common search query, but this represents only about 4% of the total internet.
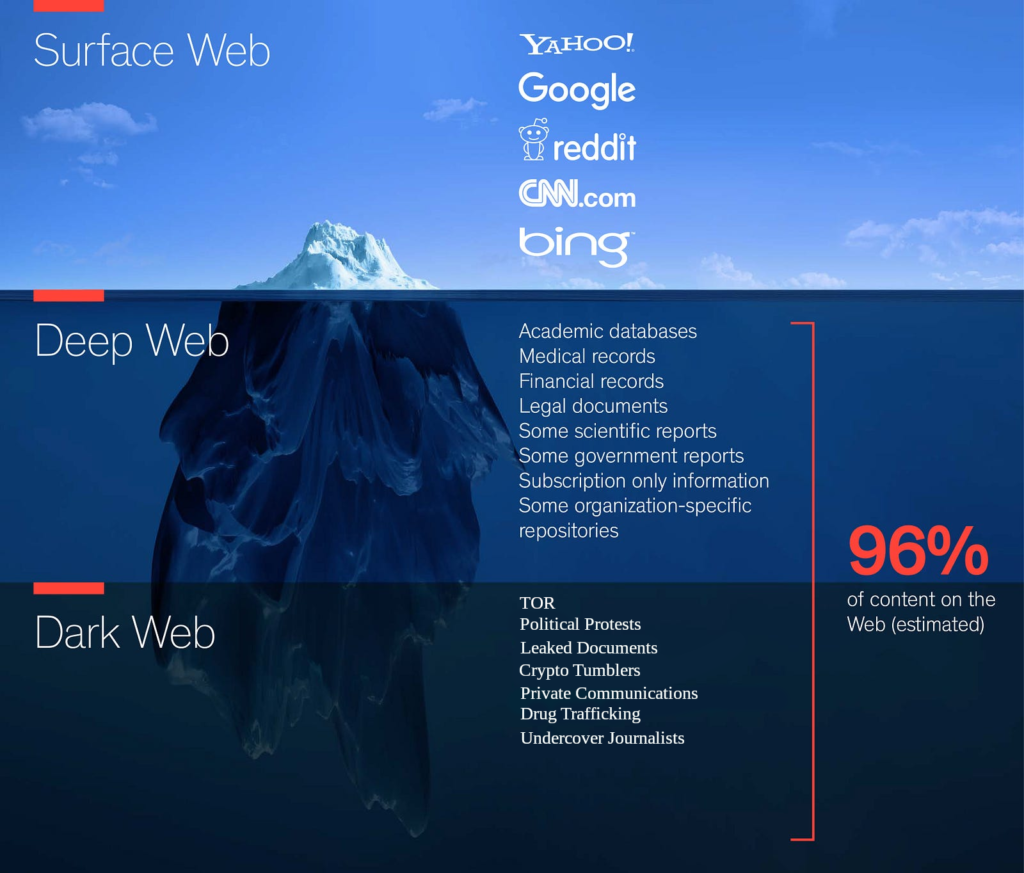
There are many advanced methods which Tor users have utilized for over a decade. Luckily, Micah Lee has developed OnionShare, which streamlines many of these methodologies for the average user (as described above), enabling them to utilize the Tor network for private communications such as sending and receiving files, hosting websites and even anonymous chat rooms.
Why is the Tor Network Private?
The way I like to think of privacy within the Tor network is within two main components: Variation (or possible addresses) which grants users an extremely high level of anonymity, and multi-layer encryption.
Variation
Each V3 onion address is 56 characters long with 32 possible combinations for each character – or every letter of the English alphabet combined with numbers 2 – 7. This means that there are 32^55 (the address will always end in ‘d’, removing one characters set) possible addresses for everyone to uses for any duration of time, which is the is the following number:
1,942,668,892,225,730,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000
If you took this total number of possible address and divided it by 999 billion, the quotient would still have 24 commas – making it highly unlikely for someone to stumble upon your address accidentally. Further, each address generate by the OnionShare client is designed for short term use, meaning that you would be a moving target within the above number of possible addresses for passive host discovery methods.
Now, even if an adversary had the ability to pick your tiny needle out of this very, VERY large hay stack, they would still have to deal with the next component protecting your privacy.
Multi-Layer Encryption
For the end-user, the Tor network works in similar manner as a proxy or VPN by masking the end-user’s IP from the website that they’re connecting to. However, unlike the proxy or VPN which typically use a single relay, Tor takes anonymity further by using 3 relays (Entry Guard, Middle Relay, Exit Relay) between the user and the end server, with each of these relays (a) in a different geographic area and (b) with a separate set of encryption.
If you want to go more in depth in this topic, be sure to check out the Mental Outlaw’s video here, as he does a fantastic job explaining how Tor works from a networking perspective:
As the final level of protection within this category, the OnionShare client allows the host user to generate private keys to your site, file share/upload or chat, which further restricts an adversary’s ability to access your content.
Install & Configuration
As always, I will be using Pop!_OS for this demonstration, which comes with Flatpak pre-installed. I prefer to use Flatpak over Snap, but both will ensure that you’re always using the newest version of OnionShare, and that it’s run from inside a sandbox.
Alternatively, it is possible install the app through your native software manager, which is Pop!_Shop on Pop!_OS or through Coanacle’s Ubuntu Software Center (Snap). This is by far the easiest method but offers the least flexibility.
If you’re using Ubuntu and would like to install via Flatpak, you’ll first need to update your system then install Flatpak with the following command:
sudo apt install flatpakNext, we’ll install OnionShare with the following command.
flatpak install flathub org.onionshare.OnionShare –yTo run OnionShare, you can search for it within your app tray or from the CLI with the following command:
flatpak run org.onionshare.OnionShare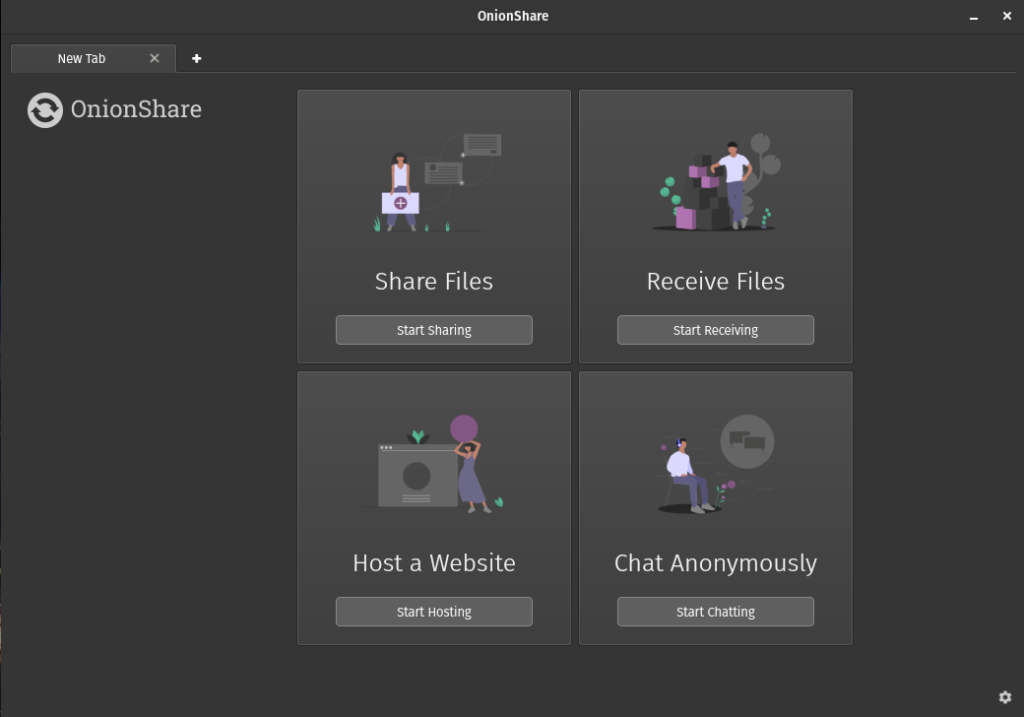
OnionShare CLI
If you are comfortable with the Linux CLI or have plans to utilize Onionshare within a cloud or cluster deployment, there is a CLI version available here: https://github.com/onionshare/onionshare/blob/main/cli/README.md
Share Files
If you click on Share from the main menu, you’ll be brought to the share options, which is very simple to navigate. In the screen-shot below, You can see that I’ve added a single image file and have have advanced settings expanded, which enables us to add a custom title and specify the time which would like for the share to be available.
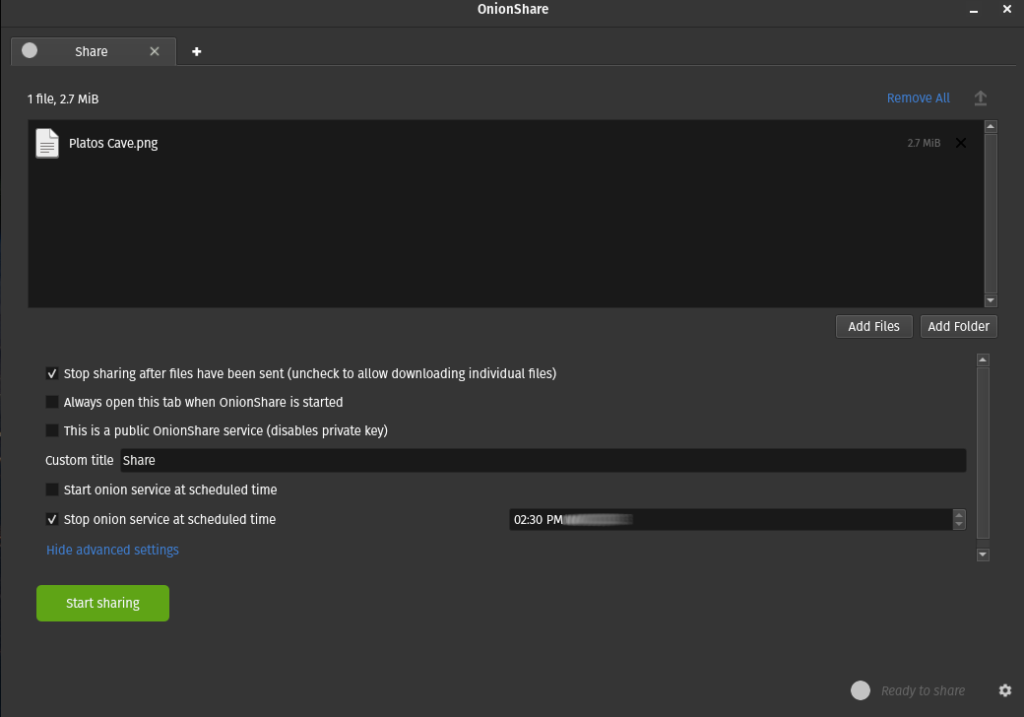
Another check box that’s worth considering during your setup is third from the top, which, as the title suggests, toggles the private key requirement for viewing files or starting a download.
When ready click the “Start sharing” button. This will create a random public onion address and private key (if you’ve left the box on default), both of which are displayed on the file share page when it loads. If you’ve enabled a stop date and time, you’ll see your remaining time counting down in the red “Stop Sharing” button, which you can click to stop anytime you like.
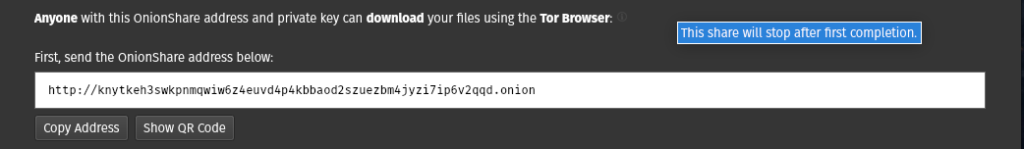
Receive Files
When choosing to receive files from your contacts through the Tor network, simply open a new tab and select “Receive Files” from the main OnionShare menu. Shown below is the receive files menu with advanced settings expanded, configured with the default directory path to save files uploaded, and a custom title for the landing page.
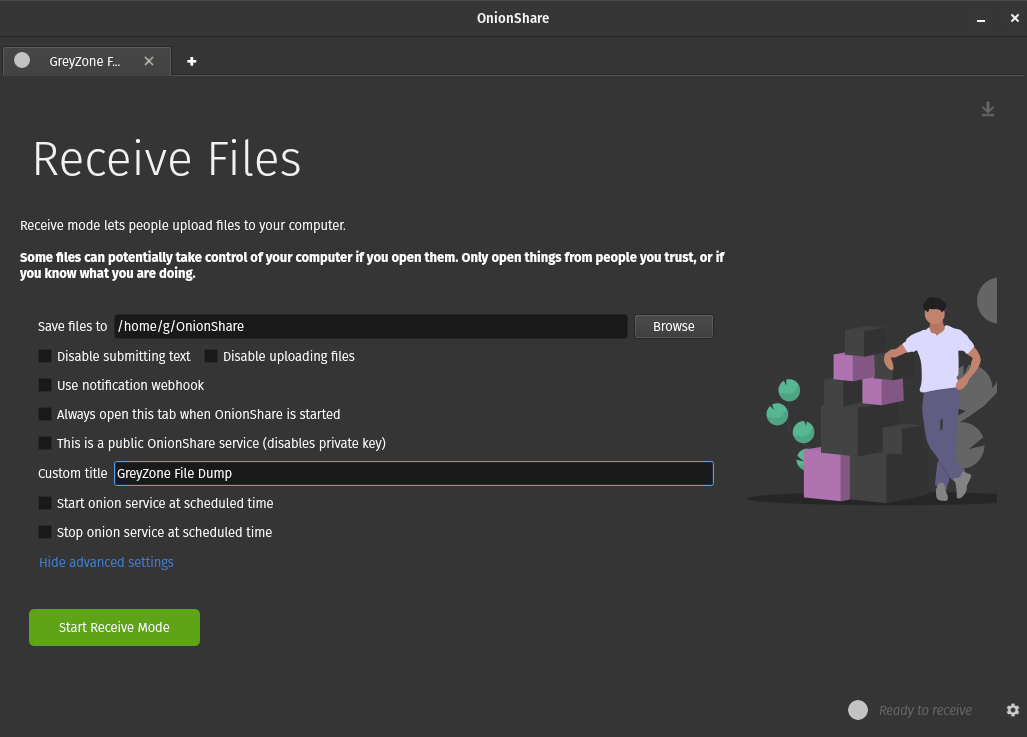
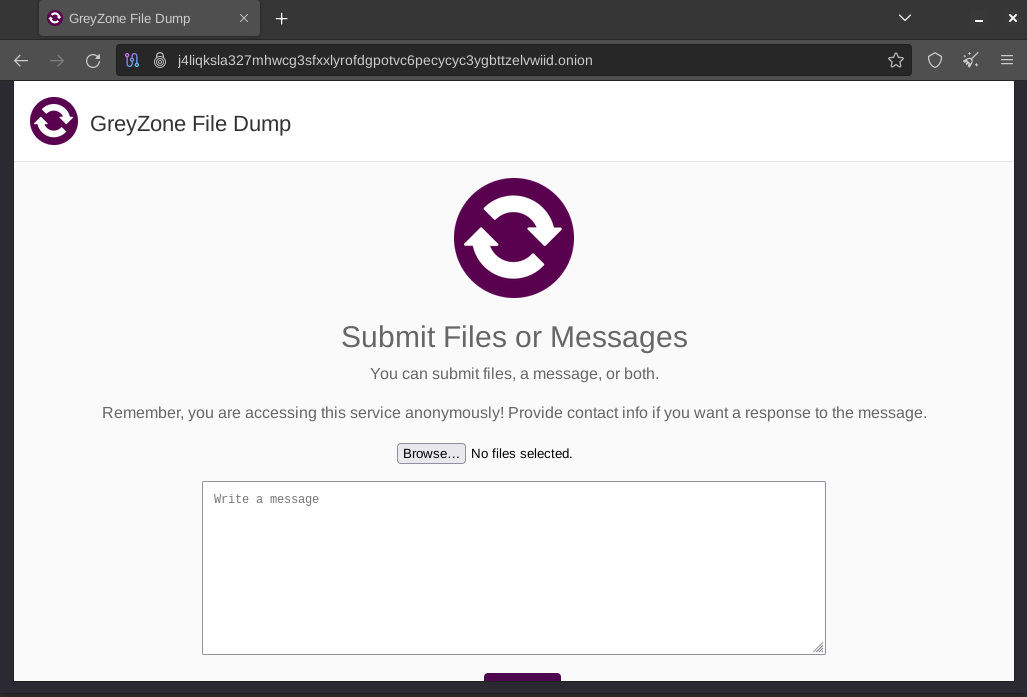
This time, I’ve decided to leave private keys enabled since I’m receiving files to my computer, but allowed the users to send text (first check box) through the share server that we’ll be starting. Next, click the green start button, and your server will be ready to receive files from anyone with the address and private keys via the Tor Browser.
Going back to the receive files menu while in a running state, your address and keys are shown below a red “stop” button, which will include a timer if you’ve enabled a time window on the setup page. As with website hosting there is a “download” icon in the upper right hand corner of the page, which expands a the menu as seen below.
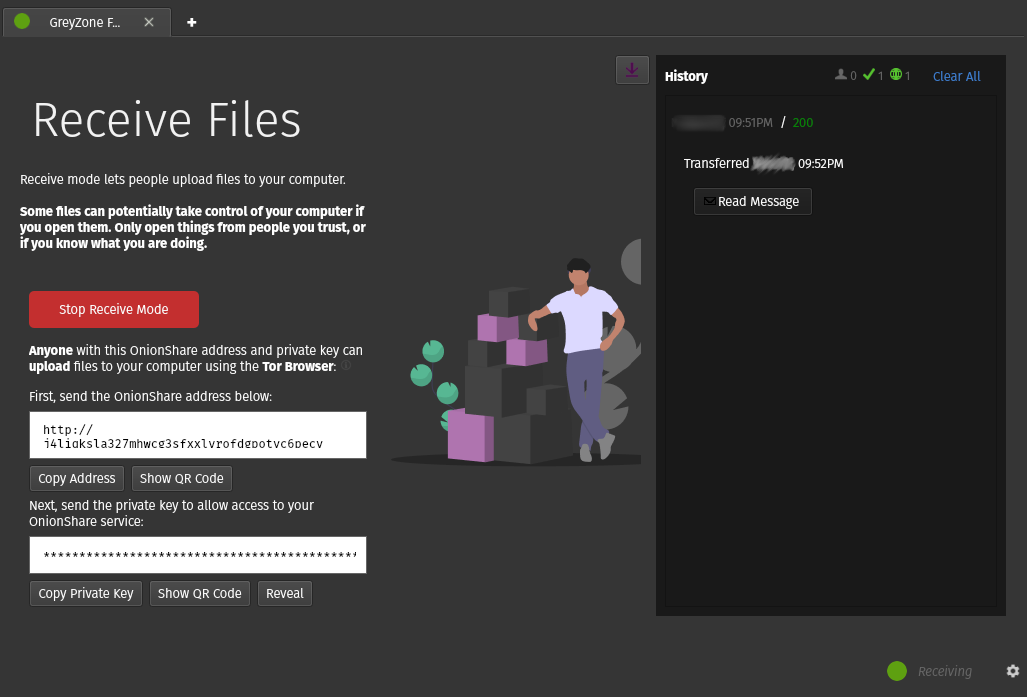
This feature allows the in host to view timestamps of the activity on your server, including activity type, which can come in handy if you’re on the look out for a particular file and/or note.
Host a Website
Hosting a website on the onion network has always been a bit different than the process you’ve probably experienced while creating a website on the clear net. With the onion network, there’s no need for domain registry, 3rd party hosting (unless you want to) or managed services. You simply create a HTML file for your static HTML site, specify the path to the HMTL file within nginx, start nginx, verify the correct proxy configuration and you’re online. Well, as you probably guessed, OnionShare has simplified this process (massively) as well.
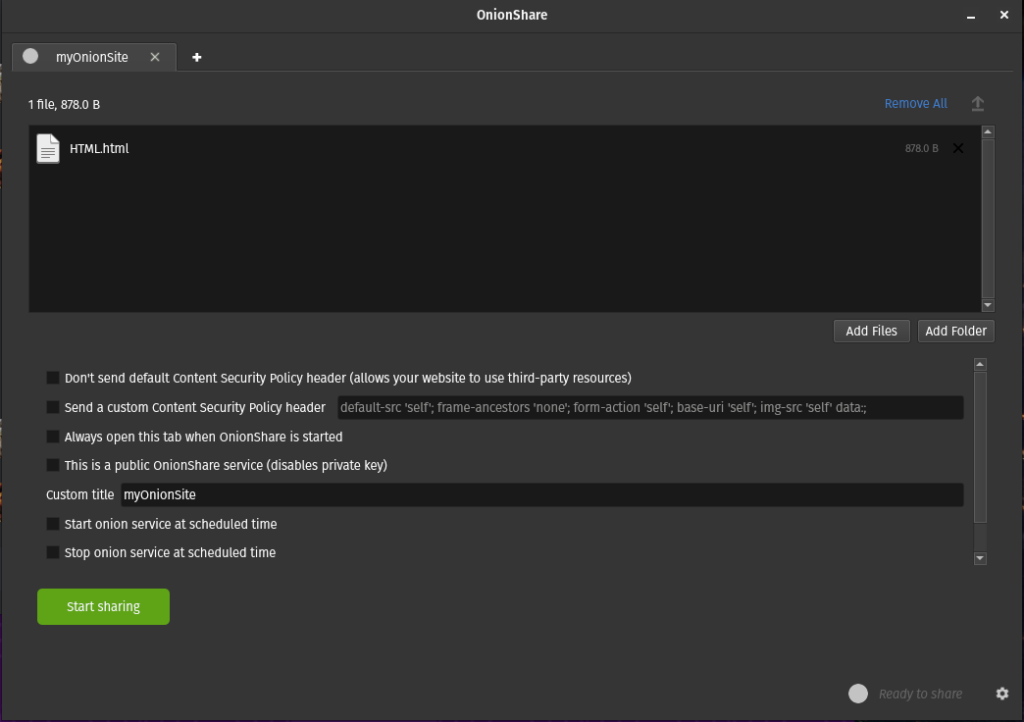
In the above image, you’ll see that I’ve uploaded a single file for demonstration purposes, but you can upload a full website file as well. You’ll notice that like the Receiving menu of OnionShare, this menu is much like that seen in the Sharing menu with a few exceptions.
- The first check box is for the Content Security Policy (CSP headers) for your site. In it’s default state, OnionShare sets a strict policy against the use of third-party resources but if you require this functionality, consider the privacy risks prior to checking the box.
- The 4th check box toggles the need for a private key. I did not want to distribute private keys for access to my demonstration site, so I check this box, but this setting might come in handy if you wish to restrict access to your site, to users you trust.
- Specific to websites, you can also set a custom title.
When ready, click the green start sharing button, and your hidden site will be online and accessible by your community before you know it.
Now on the following screen, a couple of things that are worth noting are the address and private keys (if applicable) in the bottom half of your screen, which is how you share and distribute your site. Additionally, you’ll and upload icon on the upper left corner, which when clicked, expands a simplified site history log, as shown in the image below.
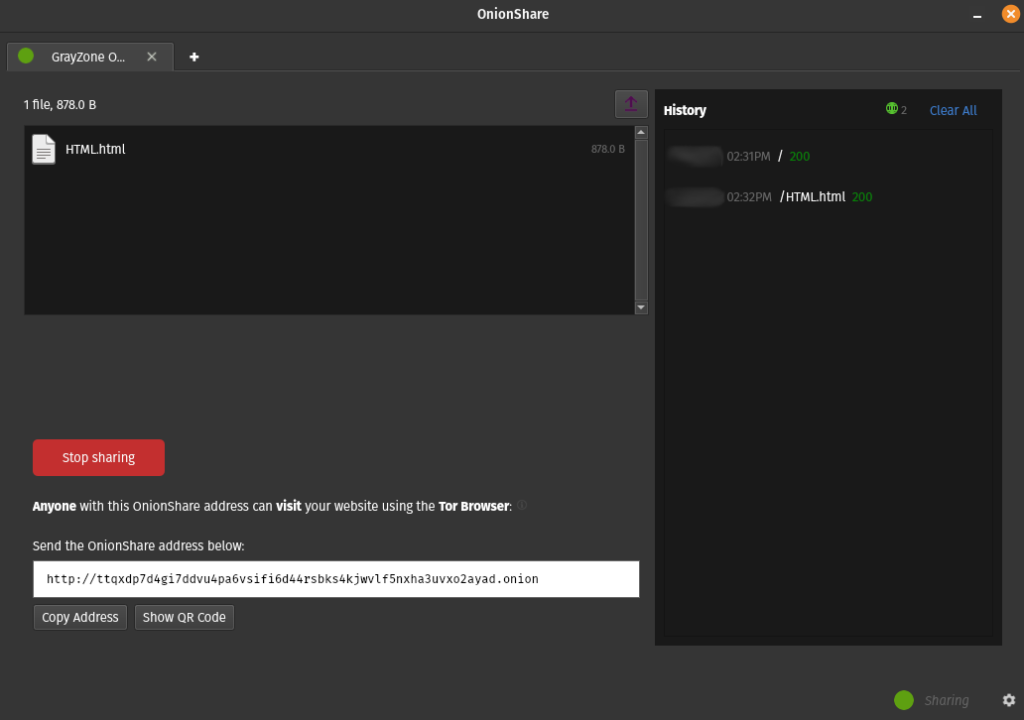
As you can see in the above image, this menu shows when I reached the website with Tor Browser for the demonstration, as well as when I accessed the file containing the site. While not detailed, this could be a handy tool for determining traffic volumes, content accessed and whether or not users are having difficulty accessing your site itself.
Disclaimer
It seems that OnionShare’s capabilities in this category were designed for rapid deployment of a temporary website. While the app is likely capable of hosting for an intermediate (if not long) term, I was unable to locate settings for known best practices which protect the host user’s anonymity. As many of you know, this is typically edited within the torrc file while configuring Tor proxychains.
Hosting a Hidden Chat Server
Hosting a chat server through OnionShare is comes with many of the same options as the other three app features. For our demonstration, we’ll disable private keys by checking the second box, enter a custom title for the chat so that our friends know that they in the right place, then click start.
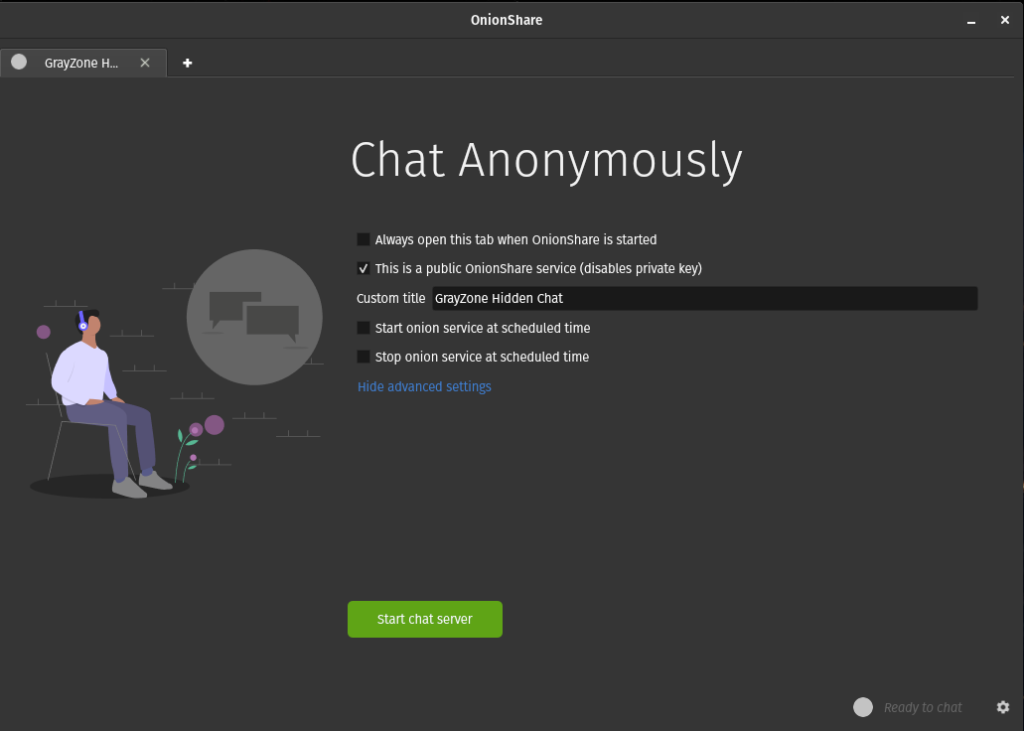
From the next screen, you’ll see address and private key (if applicable) fields similar to the file sharing and receiving menus. Also like the other features, you should see a green status button (“chatting”) in the lower right corner. This means that you chat room is online and ready for users to join through Tor Browser.
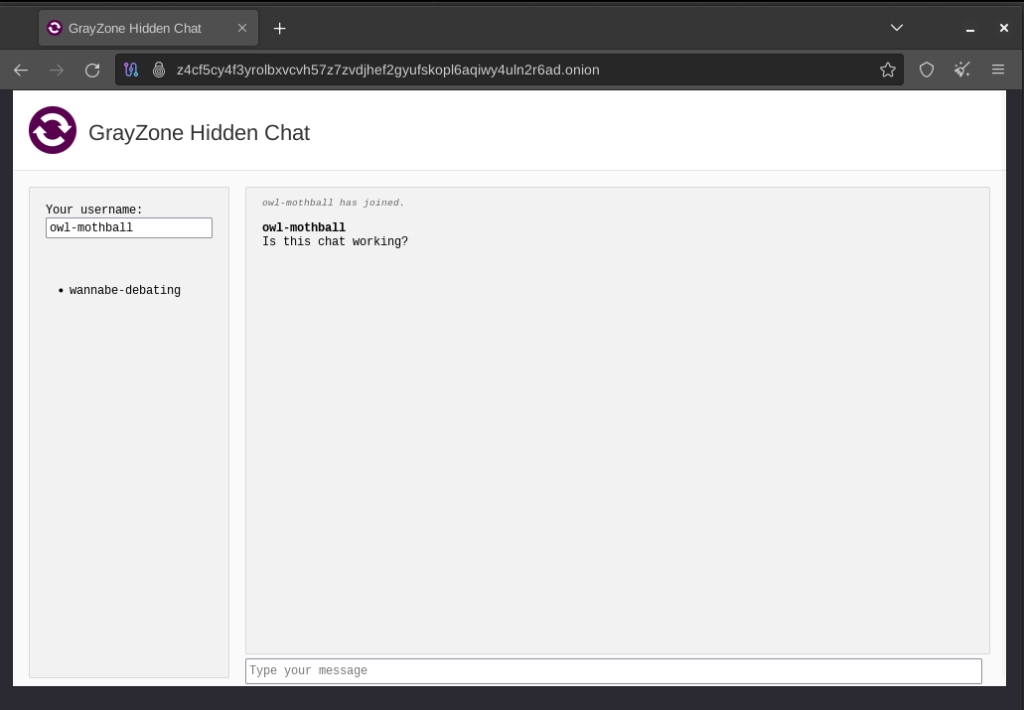
Advantages over other Chats
First and foremost, the OnionShare chat benefits from the privacy features discussed in the above section “Why is the Tor Network Private?” Additionally, and unlike Signal Messenger, WhatsApp, Discord, the desktop version of Telegram and many others; the exchange server is within the total control of the host user, and from what I can see, OnionShare does not store chat records on the host machine by default. With this said, it is an open-source program and can be modified to do so with the right technical background – so make sure that you know your host.
Closing Thoughts
I’m a massive fan of OnionShare and great admirer of Micha Lee’s work in consolidating the above capabilities within a single client, then streamlining their use. With this said, my opinion is that OnionShare was built for the purpose of (a) rapid deployment of (b) temporary resources – for which purpose it has no peers.
If you need a longer term solution for hosting a website or hosting files with a static onion address, I would recommend investigating other solutions.
Additional Resources:
- OnionShare Website: https://onionshare.org/#
- OnionShare Developer: Micah Lee on X (Twitter) https://twitter.com/micahflee
- OnionShare CLI: https://github.com/onionshare/onionshare/blob/main/cli/README.md
- Mental Outlaw: How Tor Works: https://www.youtube.com/watch?v=79m7mX3rC8Q&t=1s