Think-tanks, politicians and mainstream media sources often push the narrative that all crypto-currencies are untraceable, highlighting their use as the preferred medium in cyber-crime events – namely ransomware attacks. I always found this a bit strange given the mission statement of most of these blockchains, which is to produce a more transparent payment and audit system.
Regardless, this widespread belief has made some aspects of my past OSINT investigations much easier, especially those involving crypto payouts or transfers. In this post, we’ll dig into the questions of privacy, check out some tools and their features which can be used to trace transaction, then try to put ourselves in the minds of the people who use these for nefarious purposes.
Disclaimer
This post is for educational purposes only, and does not constitute legal advice. Further, the author does not advocate the use of privacy blockchains as a way to launder money, receive illicit financing, evade taxable transactions, violate FCPA or AML laws.
Open vs. Privacy Blockchains
For many of the larger blockchains out there, all transactions can be transparently viewed and universally audited. This requires that the auditor either has a personal node on the chain they wish to view, or the use of a blockchain explorer; either of which allows the viewer to monitor any transaction in real time as well as audit previous transactions.
However, there have been several projects which were early to point the challenges that this may presents to privacy, which began working to develop blockchains which protect both the senders and recipient’s information, as well as the transaction details itself. Here’s the short version of some of the key differences:
Open ledgers
As an analyst or researcher, if you know the wallet address and who the address belongs to, you can quickly learn how much they have in their wallet, view timestamps of all transactions to and from their wallet, how much was transferred and to which other addresses. Full, universal transparency.
Privacy Coins (ex. Monero):
Opposite of the open ledger system are privacy coins. As one example, Monero(XMR) uses Ring Signatures which mix in decoy outputs to make it extremely difficult to find which of the address was the original sender. On the receiver side, Monero uses something called a Stealth Address which initiate a huge volume of random, one-time addresses that cannot be linked in any particular address – in both cases, facilitating ‘security by obfuscation’. Further, the Monero blockchain masks the volume of tokens transferred through something called Bulletproofs.
There are also blockchains out there which support a hybrid functionality of open ledger with privacy when you need it. A notable mention in this category is Zcash(ZEC).
Tracking an Open Blockchain Target
I’ve played around with quite a few tools but my favorite for quick Bitcoin and Ethereum queries (as of the time of this writing) is the explorer from Blockchain.com because it provides enough information which, when combined with a breach data database tailored for this purpose, can serve as a great pivot point in any investigation.
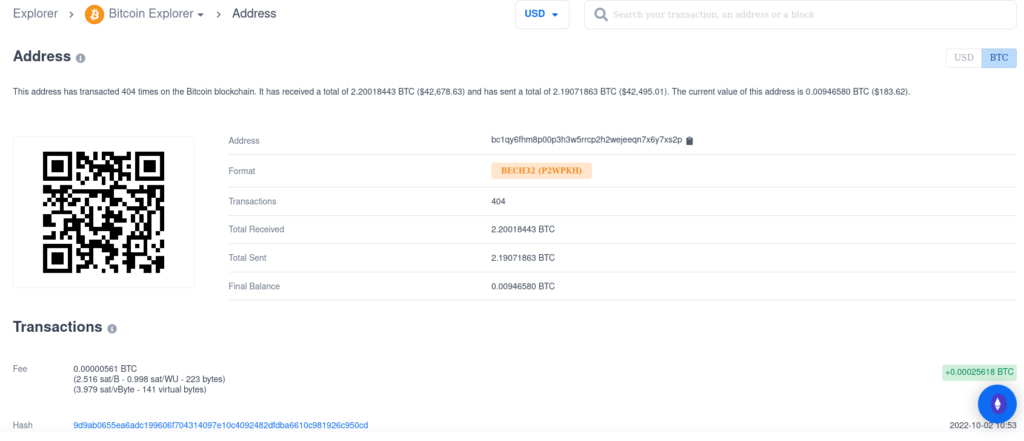
Above is a bitcoin wallet which publicly listed as a “Donate to Us” address. Do some experimenting on your own, but as you can see from the screenshot, the following are displayed:
- Total number of transactions
- Total received (in this case, Bitcoin)
- Total Sent
- Final (or current) balance.
If you scroll down, you can also see timestamps, wallet numbers, volumes sent or received and more. Again, this comes in handy if you are able to identify the wallet owner(s) through other means, or if you started your investigation with this as a known variable.
This said, the blockchain.com explorer is extremely limited in its capabilities and must be paired with additional data sets, limiting its use to a quick reference tool. For deeper analysis and intelligence, you’ll the reader will be more interested in Arkham.
Arkham Intelligence
Arkham Computer, by Arkham Intelligence it by far the most robust crypto intelligence platform that any researcher or analyst could hope for. In 2022, they claimed to contain over 300,000,000 labels and 150,000 entity pages with a complete view of each persons activity, transaction history, balance history, echange usage and more.
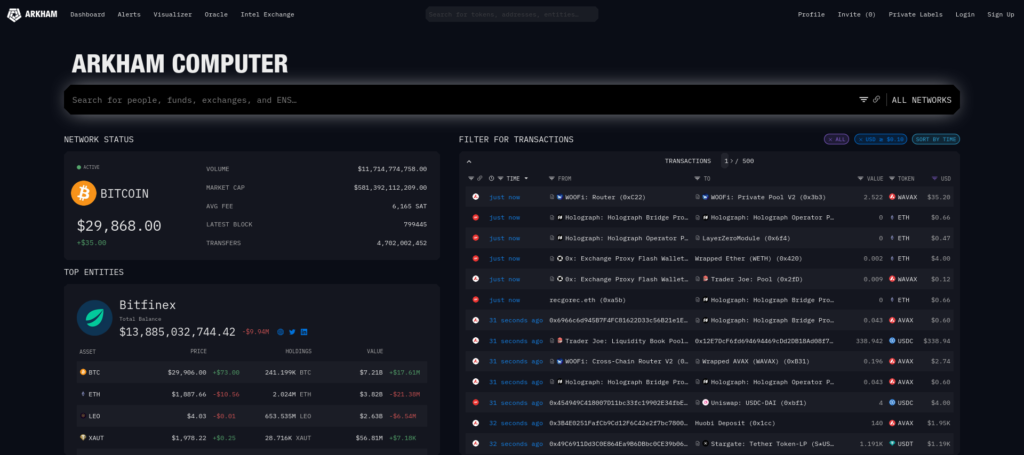
As a blockchain intelligence platform, the dashboard enables the user to set customized alerts for on chain activity of peaple, organizations and wallets for a wide range of blockchain’s and even grants numerous visualization tools which (in my opinion) expedite link analysis.
Tracking a Privacy Blockchain Target
Many of the privacy blockchains like Monero(XMR) have their own explorer applications, though transactions from the exploremonero.com site make it much more difficult to monitor a target passively or directly without detailed information on the transaction.
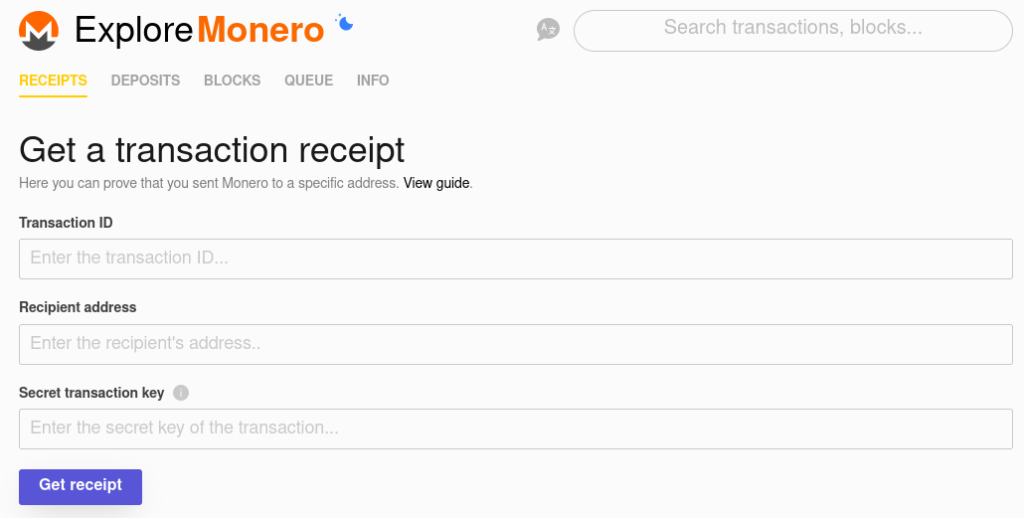
As you can see from the image above, the form for viewing a transaction requires the transaction ID, the recipient’s address and the secret key. This is probably because these tools seek only to verify a transaction between sender and receiver, rather than grant a 3rd party observer any visibility over a transaction between the two wallets.
Without some sort of persistent access to the device one of the owners use to manage their wallet, I’m not sure how you would gain meaningful information around a Monero transaction.
Tumblers
I will need dig into mechanically how this works and conduct some further testing, but it doesn’t seem unreasonable to guess that tumbler’s like crypto-tumbler.com are breaking up the total balance sent, shooting it off to wallets owned or managed by the tumbler service, then swap these out for a fee. If this is the case, then it does not make it untraceable, but it does add a lot of white noise to the equation which might be difficult to sift through, depending on the capabilities of the group performing the investigation. This would be the blockchain equivalent to loosing your tail in a crowd, as you change clothes.
While my initial inclination is to track all tokens passed from a series of addresses into the tumbler, export into Neo4j via .csv import function then attempt to track search for the volume on the other side (recipient wallets), it is not likely that (a) the ransomware gangs will use a single tumbler or (b) even if they did, their recipient wallets would be opened under the US or EU’s Anti-Money-Laundering(AML) laws – making discovering ownership pretty much impossible.
A more effective strategy would be to flag all known wallet addresses of the tumbler services through a service like Arkham, and track the final transactions from those wallets, but you will still have the challenge of dismantling money mule networks, and will likely have to work with law enforcement to do so.
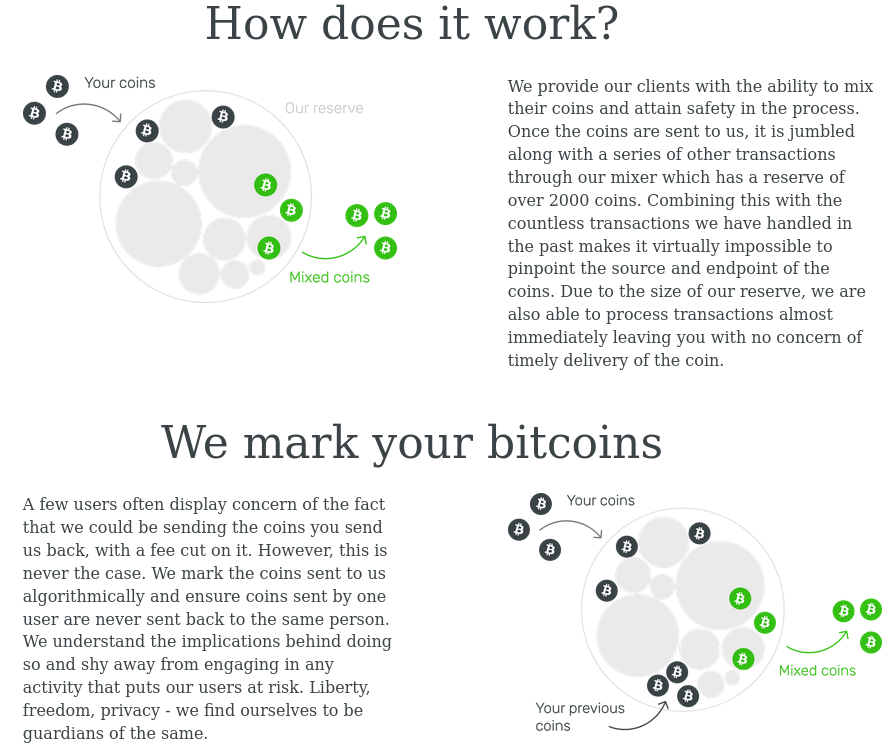
Cypto-tumbler’s standard service fee’s seem pretty reasonable for what is being offered, but it is still much higher than the transfer fees of a privacy coin like Monero(XMR).
Why Bitcoin over Privacy Chains?
So we’ve already demonstrated that Bitcoin transactions are not anonymous, but why would anyone choose to use it? If I were to put my head into the shoes of a ransomware group, I would be thinking about the psychology of the targeted victims, availability of your medium and exfiltration of funds.
The first two are interlinked: Bitcoin is wifely available and as such, the target of an attack (from individual to executive team) can likely obtain this and send it out quickly – making it a no-brainer if faced with interrupted operations. I’m sure that the Saudi’s would have loved to pay up during the Shamoon attacks in 2012.
When it comes to exfiltration of regular Open-Blockchain tokens, there are some extra steps that need to be taken, but with a little planning and API access to automate your wallets, it’s much easier to move than a duffel bag or pelican box full of paper cash, you do not need to meet anyone for a hand off and SWIFT cannot stop the transfer. It might ultimately end up as a privacy token before being cashed out.
Closing Thoughts
Be sure to shoot me a message if you’d like to work together on additional research into the above. In the future, I’ll likely write on post on Arkham, as I believe it’s a great tool for us based security and investigation teams, specifically those looking to detect insider threats.
